Any links to online stores should be assumed to be affiliates. The company or PR agency provides all or most review samples. They have no control over my content, and I provide my honest opinion.
Did you know that the cybercrime economy enjoys a hefty profit of 1.5 trillion US dollars every year?
This tells us that the state of cybersecurity is in a dire situation. In fact, it has also been reported that security breaches have increased by 11% over the last few years.
What these statistics further signify is that your precious data isn’t safe on the internet anymore. What type of data are we talking about? It is the data that you share on your social profiles, on online shopping or banking portals, forums, communities, etc.
Unfortunately, cyber-attackers can get their hands on all these data through various nefarious means.
If you wish to keep your data away from the reach of cyber goons, you need a virtual private network. These tools allow us to keep our devices as well as the data it contains completely secure against unauthorized access.
Moreover, they are available for different operating systems such as Windows VPN, Android, Linux, routers, set-top boxes as well as VPN for gaming consoles. It gives us the utmost convenience of protecting our device in our home.
Read on to find out more about some common cyber threats and how VPNs help us protect our data against it.
Types of Cyber Threats You Need to be Wary Of
Cyber threats aren’t limited to corporate infrastructures. In fact, household networks are also equally exposed to the dangers of cyber-attacks.
Moreover, cybercriminals know several ways to steal your personal information, credit card, social security number, etc. Let’s take a quick look at the common types of attacks that cybercriminals use:
Password Attack
There are many ways hackers can get their hands on your password. For instance, they could act as an imposter and ask you to share your details with them. Similarly, they can either gain access to a service’s password database or simply guess the password. After all, a good number of users still use “123456789” as their password.
Regardless, hackers can also carry out a brute-force attack where they can apply an algorithm that tests hundreds of thousands of passwords until it hits the right one.
Man in the Middle Attack
As the name suggests, the MITM attack allows cybercriminals to hijack a network and eavesdrop on the entire back and forth transmission. MITM attacks aren’t limited to eavesdropping on the network transmission. In fact, it can even allow the attacker to modify the users’ requests.
Distributed Denial of Service (DDoS) Attack
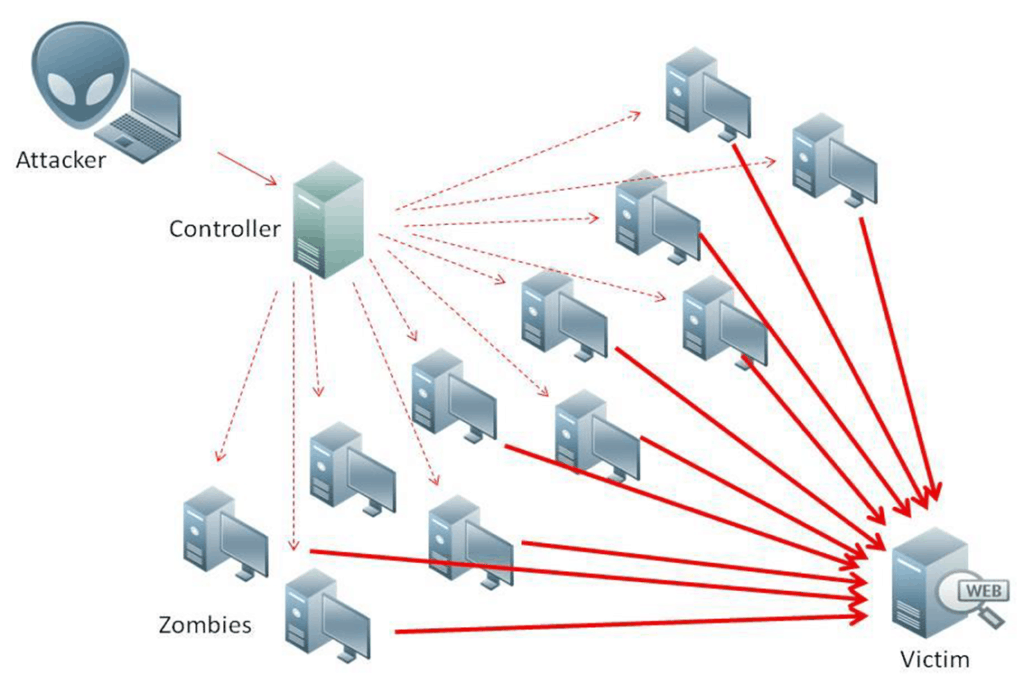
In layman terms, the attack paralyzes local networks, international servers, and even entire corporate IT infrastructures. There are a couple of ways hacker go about DDoSing their targets.
For instance, one of the most common ways hackers conduct DDoS attacks is via Botnets. They first infect a high volume of machines with malware and then when the need arises, they turn those infected machines into malicious bots that are then used to send an unimaginably high volume of traffic to the target machine to render it useless for a while.
Apart from the attacks listed above, there are dozens of other attacks that hackers can use to infiltrate a device and steal data.
What is a VPN?
VPNs stand for Virtual Private Networks. These are security tools that allow users to browse the internet on vulnerable or unsecure networks in a secure manner. The tool uses state-of-the-art handshake algorithms, data authentication methods, and encryption mode to make your personal data indecipherable.
You set up a VPN on your router or any desired device. When your device makes a request, the data which is sent from your device to the Internet gateway becomes encrypted. As a result, your data remains protected against hackers even if there’s a security breach.
What Can It Do for You?
Virtual private networks can help you in several ways. First and foremost, the tool gives you peace of mind when it comes to securing your traffic or communication on the internet. And, it does so by using military-grade encryption.
Moreover, the same tool is also used for making all your online activities completely anonymous. With the combination of encryption and anonymous IPs, you can ditch the prying eyes of your ISP and other services.
VPN services are also commonly used for bypassing geo-restrictions and even government-imposed online censorships. By using IPs from different server locations, users can virtually spoof their location and gain access to the content they desire.
Privacy, security, and accessibility are all the core benefits of a VPN. However, there’s more to a VPN than meets the eye. For instance, online gamers also use VPN services to reduce their ping and latency so that they can get a smooth gaming experience.
Final Thoughts
Cybersecurity isn’t an issue that could be left ignored. It is because if we do that, we will see even a further hike of cyber attacks every year.
I am James, a UK-based tech enthusiast and the Editor and Owner of Mighty Gadget, which I’ve proudly run since 2007. Passionate about all things technology, my expertise spans from computers and networking to mobile, wearables, and smart home devices.
As a fitness fanatic who loves running and cycling, I also have a keen interest in fitness-related technology, and I take every opportunity to cover this niche on my blog. My diverse interests allow me to bring a unique perspective to tech blogging, merging lifestyle, fitness, and the latest tech trends.
In my academic pursuits, I earned a BSc in Information Systems Design from UCLAN, before advancing my learning with a Master’s Degree in Computing. This advanced study also included Cisco CCNA accreditation, further demonstrating my commitment to understanding and staying ahead of the technology curve.
I’m proud to share that Vuelio has consistently ranked Mighty Gadget as one of the top technology blogs in the UK. With my dedication to technology and drive to share my insights, I aim to continue providing my readers with engaging and informative content.







