Any links to online stores should be assumed to be affiliates. The company or PR agency provides all or most review samples. They have no control over my content, and I provide my honest opinion.
The need for secure remote access to self-hosted services has grown substantially in recent years. Whether you’re managing a homelab, running business applications, or maintaining development environments, exposing these services to the internet requires careful consideration of security, privacy, and ease of management. Two solutions that address these needs are Cloudflare Tunnels and the newer, open-source alternative Pangolin.
Understanding Tunneled Reverse Proxies
Before diving into the specifics of each solution, it’s worth understanding what a tunneled reverse proxy is and why it matters for secure remote access.
What is a Tunneled Reverse Proxy?
A tunneled reverse proxy creates a secure connection between your private services and the public internet without requiring traditional port forwarding or exposing your network directly. The proxy sits between external users and your internal services, handling incoming requests and routing them appropriately while adding layers of security and access control.
Traditional methods of exposing services often involve:
- Port forwarding through your router
- Managing static IP addresses
- Configuring NAT settings
- Dealing with ISP restrictions
Tunneled reverse proxies eliminate these requirements by establishing outbound connections from your private network to a proxy server, which then handles incoming traffic securely.
Key Security Considerations
Reverse proxies can implement several important security controls:
- Authentication and authorization: Verifying user identities and controlling access to resources
- Rate limiting: Preventing abuse by limiting request frequency
- Web Application Firewall (WAF): Filtering malicious traffic
- Content caching: Reducing server load and improving performance
- SSL/TLS termination: Managing encryption between clients and services
Both Cloudflare Tunnels and Pangolin implement these security features, but with different approaches and trade-offs.
Cloudflare Tunnels Overview
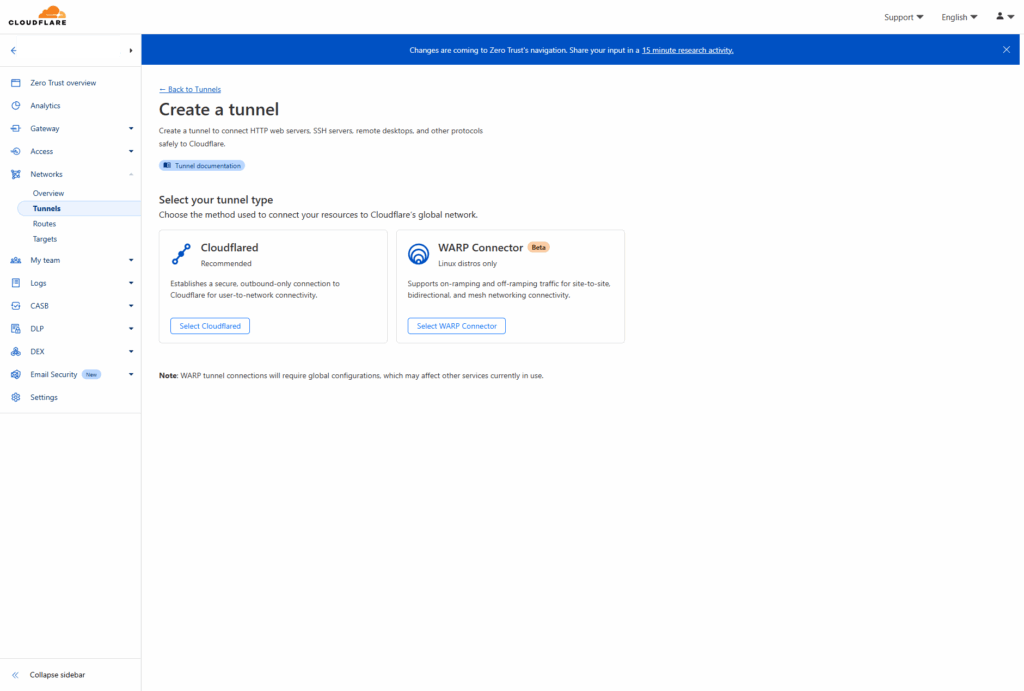
Cloudflare Tunnels (formerly Argo Tunnel) is a service that creates secure outbound connections from your origin servers to Cloudflare’s edge network, allowing you to expose web services without opening inbound ports on your firewall.
How Cloudflare Tunnels Works
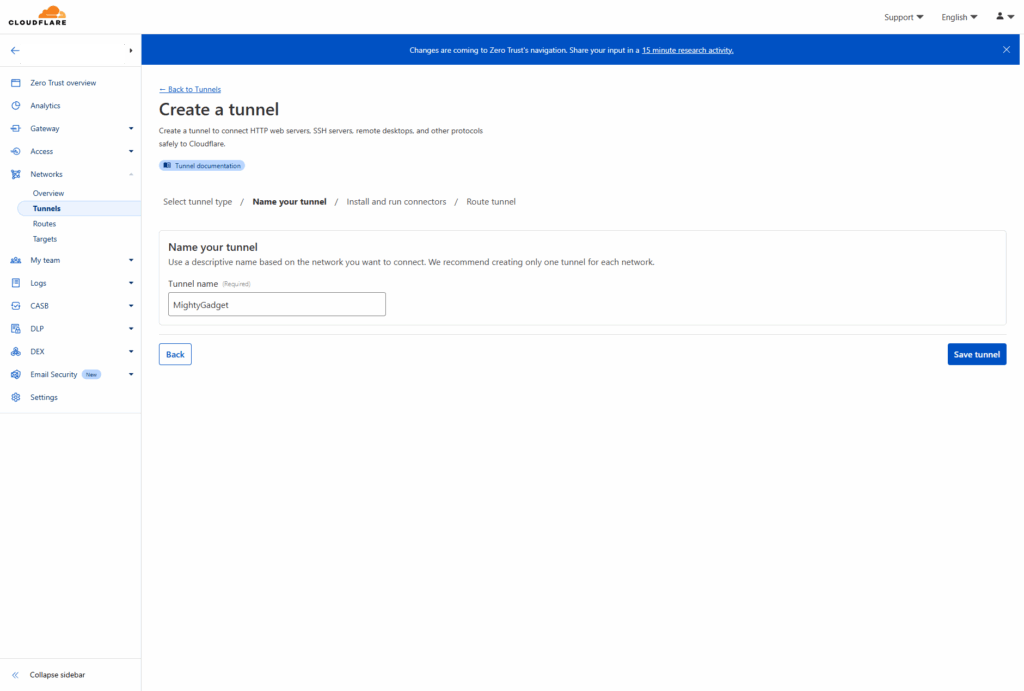
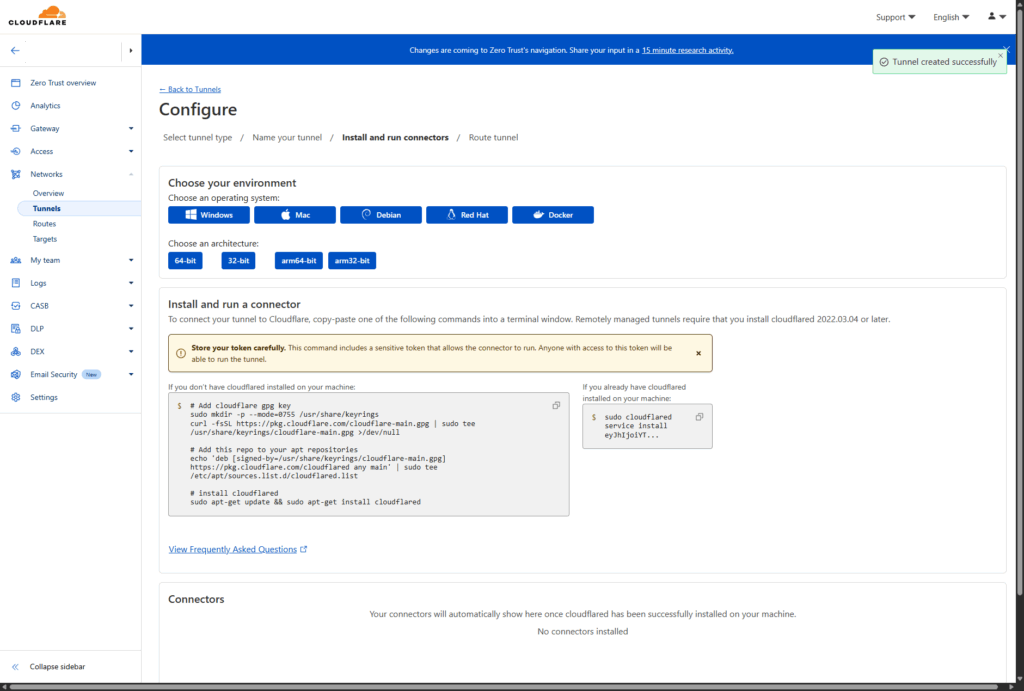
Cloudflare Tunnels operates by running a lightweight daemon called cloudflared on your origin server. This daemon establishes an outbound connection to Cloudflare’s edge network, creating a secure tunnel through which traffic can flow to your services.
When a user makes a request to your domain, Cloudflare’s edge servers receive the request, apply security policies, and then route the validated request through the established tunnel to your origin server. The response follows the same path back to the user.
Key Features of Cloudflare Tunnels
Cloudflare Tunnels offers several notable features:
- Zero trust security model: All requests are authenticated and authorized before reaching your services
- No exposed IP addresses: Your origin server’s IP address is never exposed to the internet
- Automatic SSL/TLS: Cloudflare manages certificates and encryption
- Integration with Cloudflare’s security stack: Including WAF, DDoS protection, and bot management
- Support for HTTP, HTTPS, and TCP services: Allowing a wide range of applications to be exposed
- Simple management: Through web UI or command-line interface
Permissions and Management
Cloudflare Tunnels uses two primary files to control permissions:
- Account certificate (
cert.pem): Issued when you log in tocloudflared, allowing management of all tunnels for an account - Tunnel credentials file (
<TUNNEL-UUID>.json): Specific to a single tunnel, allowing only the running of that tunnel
This separation allows administrators to share tunnel credentials with users who need to run tunnels without granting them full management capabilities.
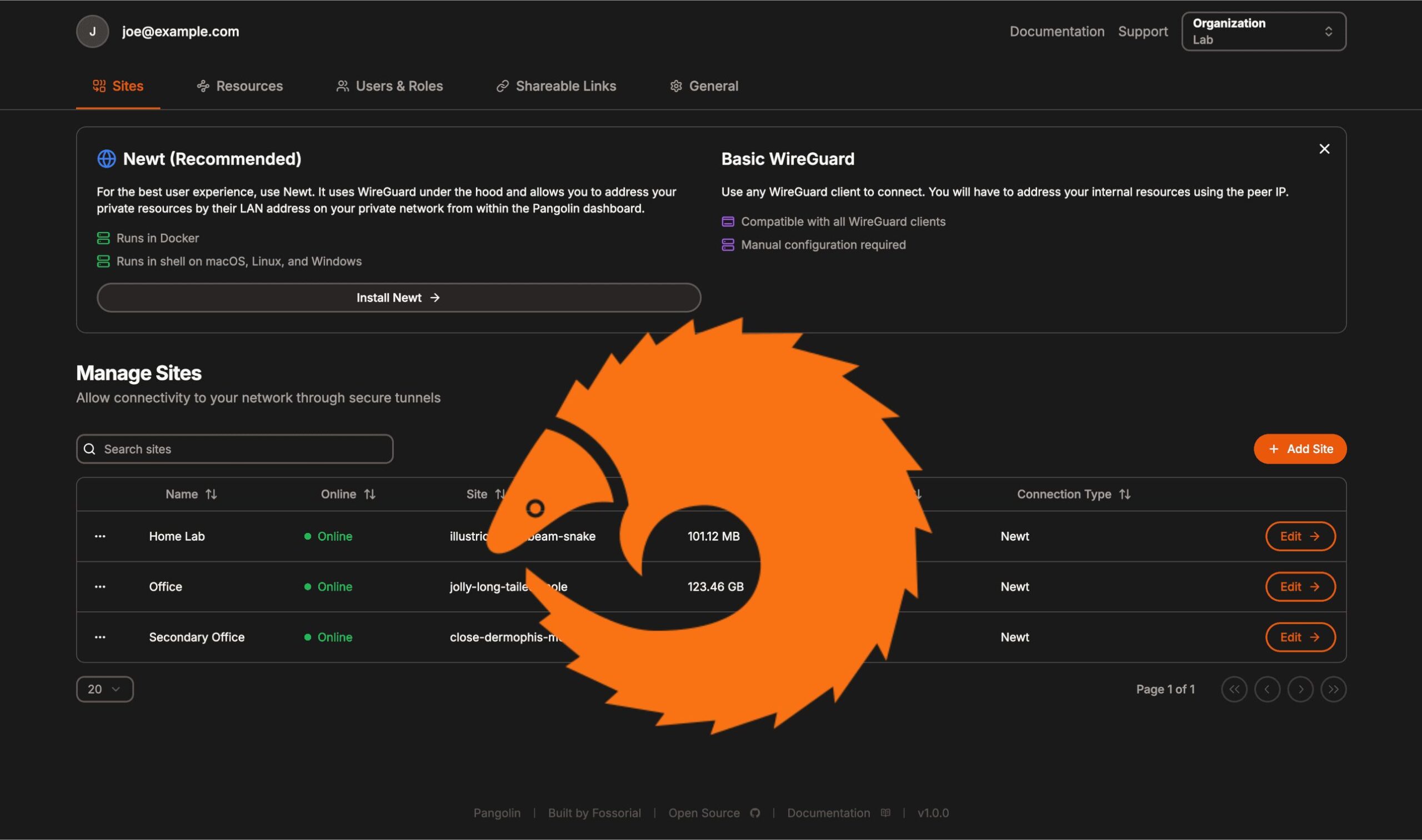
Pangolin: The Self-Hosted Alternative
Pangolin is an open-source, self-hosted tunneled reverse proxy with built-in identity and access control. Released in version 1.0 in early 2025, it aims to provide similar functionality to Cloudflare Tunnels while giving users full control over their infrastructure.
How Pangolin Works
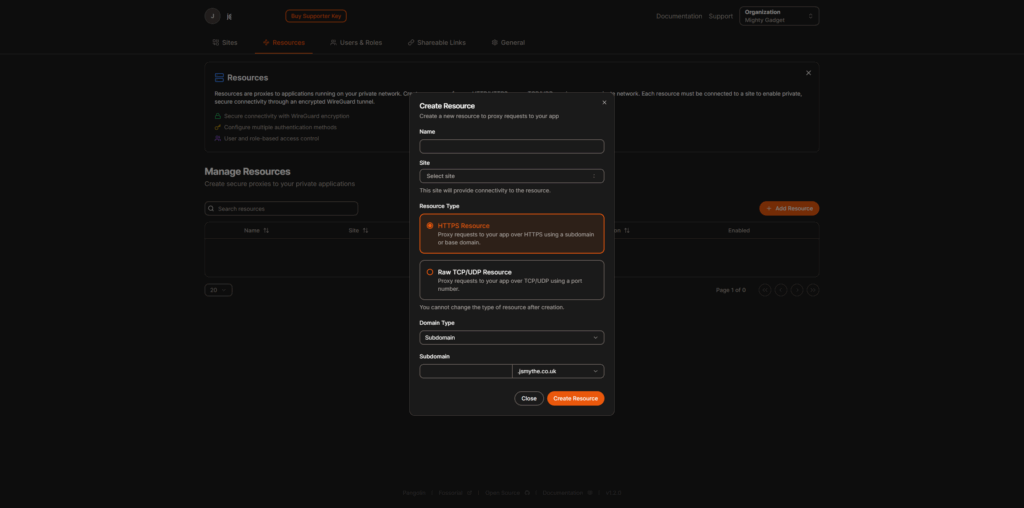
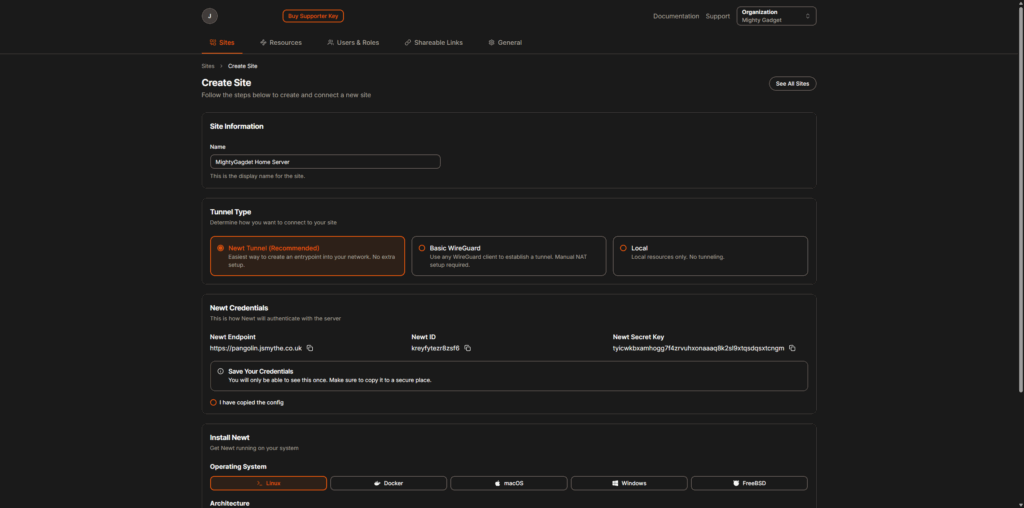
Pangolin functions as a central hub that connects isolated networks through encrypted tunnels. It uses WireGuard for secure communication between the central server and client sites, allowing you to expose services without opening inbound ports.
The architecture consists of several components:
- Pangolin: The web front-end and management interface
- Traefik: A reverse proxy that handles routing and SSL
- Badger: A component that interfaces between Pangolin and Traefik
When you configure a resource in Pangolin, it updates Traefik’s configuration via an API, creating the necessary routes and access controls. External users connect to your Pangolin server, which then routes traffic through the WireGuard tunnel to your internal services.
Key Features of Pangolin
Pangolin offers a comprehensive set of features:
- Self-hosted infrastructure: Complete control over your data and configuration
- WireGuard tunneling: Secure, efficient tunneling between sites
- Multiple domain support: Use different domains for different services
- Granular access rules: Control access by IP, CIDR ranges, or URL paths
- Identity and access management: Centralized authentication with role-based access control
- CrowdSec integration: Automated threat detection and mitigation
- Automated SSL certificates: Via Let’s Encrypt
- Support for HTTP/HTTPS and raw TCP/UDP services: Accommodating various application types
- Simple dashboard UI: For easy management of sites, users, and roles
Deployment and Management
Pangolin is deployed using Docker Compose, making it relatively straightforward to set up on any cloud provider or on-premises. It includes an installation script that simplifies the setup process and adds features like CrowdSec integration.
For connecting client sites, you can use any WireGuard client or Pangolin’s custom user-space client called Newt, which is designed to provide the best experience with Pangolin.
Feature Comparison
Let’s compare Cloudflare Tunnels and Pangolin across several key dimensions to understand their strengths and limitations.
Infrastructure and Control
Cloudflare Tunnels:
- Managed service with infrastructure maintained by Cloudflare
- Limited control over the proxy infrastructure
- Relies on Cloudflare’s global edge network
- Requires moving DNS to Cloudflare
Pangolin:
- Self-hosted solution with complete control over infrastructure
- Requires maintaining your own server (typically a VPS)
- More flexible deployment options
- Works with any DNS provider
Security and Privacy
Cloudflare Tunnels:
- Traffic passes through Cloudflare’s network
- Cloudflare can decrypt and inspect traffic
- Benefits from Cloudflare’s enterprise-grade security infrastructure
- Limited privacy as a third party handles your data
Pangolin:
- Traffic stays within your control
- No third-party access to your data
- Security depends on your implementation and maintenance
- Greater privacy as all data remains under your management
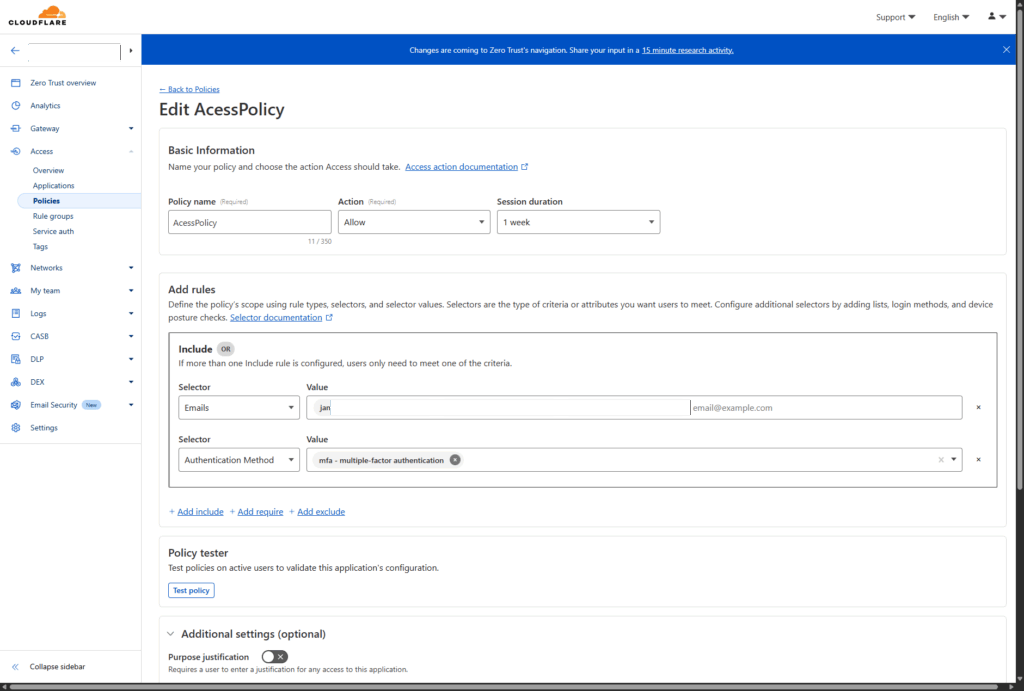
Authentication and Access Control
Cloudflare Tunnels:
- Integrates with Cloudflare Access for identity verification
- Supports various identity providers
- Zero trust security model
- Limited granular control at the proxy level
Pangolin:
- Built-in authentication and authorization
- Role-based access control
- Granular rules for IPs, CIDR ranges, and URL paths
- Support for TOTP with backup codes for two-factor authentication
- Temporary, self-destructing share links
Ease of Use
Cloudflare Tunnels:
- Simple setup through web UI or CLI
- Minimal configuration required
- Managed certificates and DNS
- Limited customization options
Pangolin:
- More complex initial setup
- Docker Compose based deployment
- Greater customization possibilities
- Intuitive dashboard for ongoing management
Cost
Cloudflare Tunnels:
- Free tier available with limitations
- Paid plans for advanced features and higher usage
- No infrastructure costs as Cloudflare manages everything
Pangolin:
- Open-source and free to use
- Infrastructure costs for hosting (typically a VPS)
- Maintenance costs in terms of time and expertise
Integration and Extensibility
Cloudflare Tunnels:
- Tight integration with Cloudflare’s ecosystem
- Limited extensibility outside Cloudflare’s offerings
- Well-documented API
Pangolin:
- Modular design based on Traefik
- Support for Traefik plugins like CrowdSec and Geoblock
- Open-source nature allows for customization
Use Cases and Suitability
Both solutions excel in different scenarios. Here’s a breakdown of when each might be the better choice:
When to Choose Cloudflare Tunnels
Cloudflare Tunnels is likely the better option when:
- You need a simple, quick setup with minimal maintenance
- Your organization already uses Cloudflare for DNS or other services
- You require enterprise-grade DDoS protection
- You have limited technical resources for managing infrastructure
- You’re comfortable with a third party handling your traffic
- Cost of infrastructure is a concern
When to Choose Pangolin
Pangolin might be preferable when:
- Data privacy and control are paramount concerns
- You have the technical capability to manage your own infrastructure
- You need highly customized access control rules
- You want to avoid vendor lock-in with a proprietary service
- You’re already managing self-hosted services and have the infrastructure in place
- You need features like granular access rules or CrowdSec integration
Setting Up Pangolin
If you’re interested in trying Pangolin, here’s a brief overview of the setup process.
Prerequisites
Before setting up Pangolin, you’ll need:
- A domain name for your Pangolin server
- A VPS or server with Docker and Docker Compose installed
- Basic knowledge of networking and Docker concepts
Installation Steps
- Prepare your server: Set up a VPS with Docker and Docker Compose installed
- Configure DNS: Point your domain to your server’s IP address
- Clone the Pangolin repository: Download the necessary files
- Run the installation script: This will set up Pangolin and optional components like CrowdSec
- Access the dashboard: Log in to the web interface to start configuring your resources
- Set up client connections: Install WireGuard or Newt on client sites to establish tunnels
Adding Resources
Once Pangolin is running, you can add resources through the dashboard:
- Create a new site in the dashboard
- Configure the connection details for the resource
- Set up access rules to control who can access the resource
- Generate and deploy the client configuration to the site hosting the resource
- Test the connection to ensure everything is working properly
Setting Up Cloudflare Tunnels
For comparison, here’s a brief overview of setting up Cloudflare Tunnels.
Prerequisites
Before setting up Cloudflare Tunnels, you’ll need:
- A domain managed by Cloudflare (requires transferring DNS to Cloudflare)
- A server or device hosting the services you want to expose
- Basic understanding of DNS and networking concepts
Installation Steps
- Move your domain to Cloudflare: Transfer DNS management to Cloudflare
- Log in to Cloudflare Zero Trust: Access the Tunnels section
- Create a new tunnel: Give it a name and follow the setup wizard
- Install cloudflared: Run the provided command on your origin server
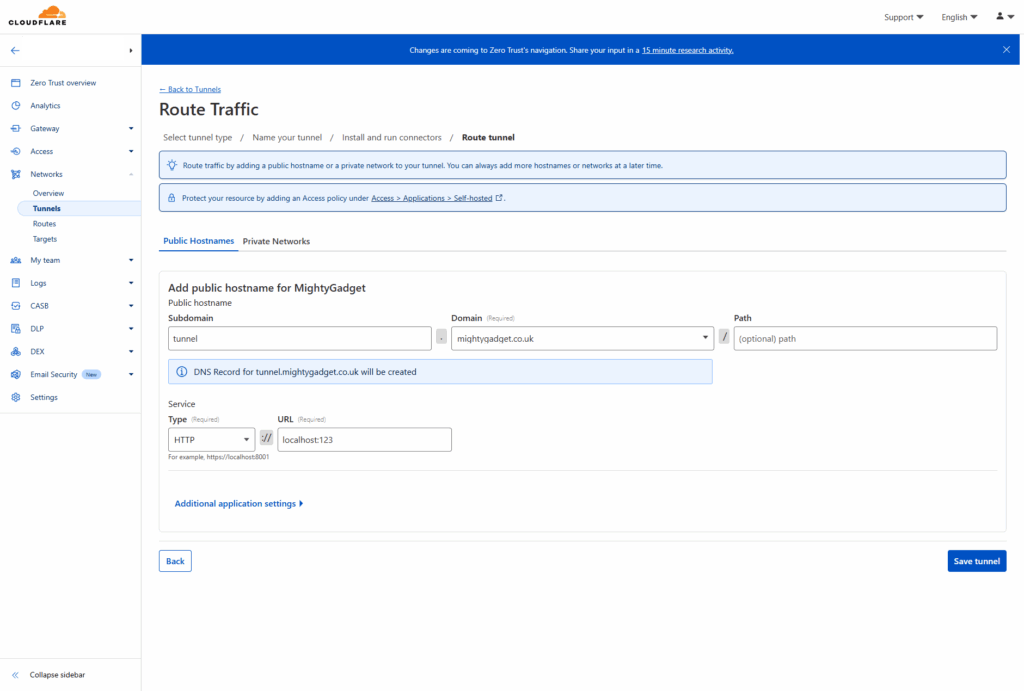
- Configure public hostnames: Map domain names to your internal services
- Test the connection: Ensure your services are accessible through the tunnel
Security Best Practices
Regardless of which solution you choose, following these security best practices will help ensure your implementation is as secure as possible:
For Both Solutions
- Implement the principle of least privilege for all access controls
- Regularly audit access logs and user permissions
- Keep all components updated with security patches
- Use strong authentication methods, preferably with multi-factor authentication
- Regularly test your security controls
For Cloudflare Tunnels
- Carefully manage your
cert.pemfile to prevent unauthorized tunnel management - Use Cloudflare Access policies to restrict who can connect to your services
- Consider implementing additional authentication at the application level
For Pangolin
- Secure your VPS with proper firewall rules and regular updates
- Implement CrowdSec to detect and block malicious activity
- Use granular access rules to limit exposure of sensitive resources
- Regularly back up your Pangolin configuration
- Monitor system logs for unusual activity
Future Developments
Both platforms continue to evolve, with new features and improvements on the horizon.
Pangolin Roadmap
Pangolin’s recent 1.0 release included several significant features, and future plans include:
- Expanded authentication options (LDAP, Google authentication)
- Enhanced monitoring and analytics
- Improved performance and scalability
- Additional security integrations
Cloudflare Tunnels Evolution
Cloudflare continues to enhance its tunneling solution with:
- Tighter integration with other Cloudflare services
- Improved performance and reliability
- Enhanced management capabilities
- Additional protocol support
Conclusion
Both Cloudflare Tunnels and Pangolin offer powerful solutions for securely exposing private services to the internet without traditional port forwarding. The choice between them ultimately comes down to your specific requirements, technical capabilities, and priorities regarding control, privacy, and ease of use.
Cloudflare Tunnels provides a polished, managed service that’s easy to set up and maintain, making it ideal for users who prioritise simplicity and don’t mind relying on a third-party service. Its integration with Cloudflare’s broader security ecosystem offers robust protection against various threats.
Pangolin, as a self-hosted alternative, gives you complete control over your infrastructure and data, with no dependency on external services. Its granular access controls and integration with tools like CrowdSec make it a powerful option for those with the technical capability to manage their own infrastructure.
As remote access needs continue to evolve, both solutions will likely adapt and improve, offering even more capabilities for secure, efficient access to private resources. The emergence of open-source alternatives like Pangolin demonstrates the growing demand for self-hosted, privacy-focused solutions in the tunneling space, giving users more options to meet their specific needs.
Whether you choose the managed convenience of Cloudflare Tunnels or the self-hosted control of Pangolin, implementing a tunneled reverse proxy with proper access controls is a significant improvement over traditional port forwarding, enhancing both security and flexibility for remote access to your private services.