Any links to online stores should be assumed to be affiliates. The company or PR agency provides all or most review samples. They have no control over my content, and I provide my honest opinion.
The YubiKey 5 series has been around for several years and is generally regarded as the gold standard of hardware security keys.
While I have used a YubiKey in the past, I never committed to it; however, they have recently become much more appealing to me.
In recent years, I have moved away from LastPass for passwords and (mostly moved from) Authy for MFA due to security breaches.
I recently started work at an MSP providing IT support for a variety of clients. Every client uses MFA, and every service I use as part of my job requires MFA.
On top of that, I have MFA enabled on as many services as possible for personal use.
This has left me with a mess of apps with some lingering accounts in Authy, Microsoft Authenticator for work, Bitwarden for passwords and some MFA codes for personal use, Ente Auth as my main MFA app, then Keeper for passwords and MFA for work. Plus, a load of Passkeys are saved with Google.
Due to my work with Mighty Gadget, I swap my phone a lot and recently realised it wasn’t easy to migrate Microsoft Authenticator codes to a new phone, which nearly locked me out of a lot of important accounts (I overlooked the restore-from-backup option).
Therefore, hardware keys have become increasingly appealing in recent months. At the very least, they can provide a good backup MFA solution for any services that allow you to use multiple MFA options.
The Yubikey 5C Nano is particularly appealing as I lose things for fun, and this tiny key is designed to stay inserted into your USB-C port permanently.
| Preview | Product | Rating | Price | |
|---|---|---|---|---|

| Yubico - YubiKey 5C Nano - Two-factor authentication (2FA)... |
£65.28 | Buy on Amazon |
Features
Broad ecosystem
Compatible with a wide range of identity providers including Centrify, Ping, Okta and Google, allowing for immediate deployment.
Configurable
Straightforward configuration options for multiple protocols across computers, networks, and various online applications and services.
Easy to use
Authentication requires no battery or network connection – users simply insert the device and tap to verify their identity.
High quality
Constructed with durable glass-fibre reinforced plastic. Rated IP68 for water and dust resistance, crush resistant, and designed without batteries or moving parts for maximum reliability.
Trusted partner
YubiKey is the authentication solution of choice for 9 of the top 10 internet companies and has millions of users worldwide.
Multi-protocol
Full support for a comprehensive range of security standards including WebAuthn, FIDO2 CTAP1, FIDO2 CTAP2, FIDO2 CTAP2.1, Universal 2nd Factor (U2F), Smart card (PIV-compatible), Yubico OTP, OATH – HOTP (Event), OATH – TOTP (Time), OpenPGP, and Secure Static Passwords.
Works with
Compatible with major platforms and services including Facebook, Twitter, Google Account, Microsoft account, Salesforce.com, Dropbox, Keeper®, 1Password, Bitwarden Premium, AWS Identity and Access Management (IAM), Duo Security, Forgerock, Idaptive, Microsoft Azure AD, Okta, OneLogin, and Ping Identity.
Yubico authenticator app
Works with the Yubico Authenticator App, providing a secure authentication experience across both mobile and desktop platforms.
Specification
| Specification Category | Details |
| Device Information | |
| Productivity & Communication | Google Account, Microsoft account, Salesforce.com |
| Password Managers | Keeper®, LastPass Premium, 1Password, Bitwarden Premium |
| Cloud Storage | Dropbox |
| Social | Facebook, Twitter |
| Identity & Access Management | AWS IAM, Duo Security, Forgerock, Idaptive, Microsoft Active Directory, Microsoft Azure AD, Okta, OneLogin, Ping Identity |
| Passkeys (FIDO2) Slots | 100 |
| OATH Slots | 64 |
| PIV Certificates | 24 |
| OTP Seeds | 2 |
| Firmware | 5.7 |
| Standards | |
| Features | Full-featured, multi-protocol |
| Security Functions | WebAuthn, FIDO2 CTAP1, FIDO2 CTAP2, FIDO2 CTAP2.1, Universal 2nd Factor (U2F), Smart card (PIV-compatible), Yubico OTP, OATH – HOTP (Event), OATH – TOTP (Time), OpenPGP, Secure Static Passwords |
| Certifications | IP68, FIDO Universal 2nd Factor (U2F), FIDO L1, FIDO L2 |
| Cryptographic Specifications | RSA 2048, RSA 3072, RSA 4096, ECC P256, ECC P384, ED25519, X2 |
Unboxing / Design

The packaging is minimal and inside, you’ll find the YubiKey 5C Nano itself, along with a brief instruction leaflet.
The design of the YubiKey 5C Nano is remarkably small, even compared to other YubiKey models. The device is designed to be as unobtrusive as possible, allowing it to remain plugged into a USB-C port without interfering with the use of adjacent ports or the device’s mobility.
The USB-C connector is sturdy and fits snugly into ports, providing a secure connection. The device’s body is smooth and featureless except for a small, circular gold contact point on one side. This contact point is where users tap to authenticate, and it’s just large enough to be easily located by touch.
One notable design choice is the absence of any hole or attachment point for a keyring or lanyard. This is intentional, as the YubiKey 5C Nano is meant to remain plugged into a device rather than carried separately. While this might seem limiting at first, it’s a design decision that aligns with the device’s intended use case.
The YubiKey 5C Nano’s diminutive size is both its most striking feature and its potential weakness. While it’s perfect for leaving plugged into a laptop or desktop computer, its small size could make it easy to misplace if removed. Similarly, some people have highlighted that removing the nano from the USB-C port can be challenging.
Is it secure to leave the Yubikey 5C Nano permanently?
One of the primary concerns raised about the YubiKey 5C Nano is its design, which encourages users to leave the security key plugged into their computer permanently. This approach diverges from traditional security key usage, where the key is typically removed and stored separately when not in use.
The argument against leaving the YubiKey 5C Nano permanently inserted is rooted in physical security concerns. Critics argue that if a laptop or device is stolen, the thief would have access to the user’s MFA device, potentially compromising the additional layer of security that the YubiKey is meant to provide.
However, this argument overlooks several important factors:
- Multi-factor authentication: Even with physical access to the YubiKey, a malicious actor would still need to know the user’s password to gain access to protected accounts. The YubiKey is designed to be one part of a multi-factor authentication system, not a standalone security measure.
- PIN protection: Many services that use YubiKeys for authentication also require a PIN to be entered before the key can be used. This adds another layer of security, even if someone has physical access to both the device and the YubiKey.
- Remote disable: In the event of a device theft, users can typically disable their YubiKey remotely through the services they use, preventing it from being used for authentication even if a thief has physical access.
- Risk assessment: The vast majority of cyber-attacks occur remotely. While physical device theft is a concern, it’s generally a much lower risk than remote attacks like phishing or credential stuffing.
- Quick response time: Most users would quickly notice the loss or theft of a laptop or mobile device and be able to take action to disable their YubiKey long before a bad actor could realistically guess or brute force the PIN needed to use it.
- Convenience leading to consistent use: By designing the YubiKey 5C Nano to remain in the device, Yubico encourages consistent use of the security key. This can lead to better overall security practices, as users are more likely to enable and use MFA when it’s convenient.
It’s worth noting that the security model of the YubiKey 5C Nano is not fundamentally different from that of a built-in fingerprint reader or TPM chip. These are also physically part of the device and could theoretically be accessed if the device is stolen, yet they are widely accepted as security enhancements.
Ultimately, the decision to leave the YubiKey 5C Nano permanently inserted should be based on individual risk assessment. For many users, the convenience and consistent use encouraged by this design will outweigh the relatively low risk of physical device theft. However, users in high-security environments or those particularly concerned about physical device theft may prefer to remove and secure their YubiKey when not in use.
As with all security measures, it’s important to consider the YubiKey 5C Nano as part of a broader security strategy, including strong passwords, regular software updates, and awareness of phishing and other social engineering tactics.
Set Up
Setting up the YubiKey 5C Nano is a straightforward process, but it does require some initial configuration to get the most out of the device. Here’s a general overview of the setup process:
- Physical insertion: The first step is simply plugging the YubiKey 5C Nano into an available USB-C port on your device. Due to its small size, it’s designed to stay plugged in, so choose a port that won’t interfere with other peripherals.
- Driver installation: In most cases, modern operating systems will recognise the YubiKey 5C Nano automatically without needing additional drivers. However, it’s always a good idea to check for any available updates or specific drivers from Yubico’s website.
- Yubico Authenticator App: While not strictly necessary for all functions, installing the Yubico Authenticator App on your computer or mobile device can greatly enhance the YubiKey’s functionality. This app allows you to manage OATH-TOTP codes directly on your YubiKey.
- Service configuration: The next step is to configure the YubiKey with the various services you want to secure. This process will vary depending on the service, but generally involves:
- Logging into your account
- Navigating to the security or two-factor authentication settings
- Selecting the option to add a security key
- Following the prompts to register your YubiKey, which usually involves touching the key when prompted
- Testing: After setting up each service, it’s crucial to test the authentication process to ensure everything is working correctly. Try logging out and back in to verify that the YubiKey is being recognised and functioning as expected.
- Backup options: While setting up your YubiKey, it’s important to also configure backup options. This might include setting up backup codes, configuring a second YubiKey, or enabling alternative 2FA methods. This ensures you won’t be locked out of your accounts if you lose access to your YubiKey.
- PIN setup: For services that support it, setting up a PIN for your YubiKey adds an extra layer of security. This prevents unauthorised use of the key if someone gains physical access to both your device and the YubiKey.
- OpenPGP and PIV setup: For advanced users, the YubiKey 5C Nano supports OpenPGP and PIV. Setting these up requires additional steps and is typically done using command-line tools or specialised software.
It’s worth noting that the setup process might seem daunting at first, especially if you’re securing multiple accounts. However, the time investment upfront pays off in enhanced security and ease of use in the long run. Yubico provides detailed documentation and guides for various services and use cases, which can be invaluable during the setup process.
Remember, the goal is to integrate the YubiKey into your daily digital life in a way that enhances security without becoming a burden. Take the time to set it up properly, and you’ll find that it quickly becomes an seamless part of your authentication routine.
Yubikey Compatible Services
The YubiKey 5C Nano is compatible with a wide range of services, making it a versatile tool for securing various aspects of your digital life. Here’s an overview of some key categories and specific services that work well with the YubiKey:
Password Managers
Password managers are a crucial component of good security hygiene, and many popular options support YubiKey integration:
- LastPass Premium
- 1Password
- Dashlane
- Bitwarden Premium
- Keeper
Using a YubiKey with your password manager adds an extra layer of security to your entire password ecosystem.
Cloud Storage
Securing your cloud storage is essential, especially if you store sensitive documents. Several major cloud storage providers support YubiKey:
- Dropbox
- Google Drive (via Google Account)
- OneDrive (via Microsoft Account)
Social Media
While not all social media platforms support hardware security keys, some major ones do:
Email accounts are often the keys to the kingdom for other services, making them crucial to secure:
- Gmail (via Google Account)
- Outlook.com (via Microsoft Account)
- ProtonMail
Developer Tools
For developers, securing access to code repositories and cloud services is paramount:
- GitHub
- GitLab
- Bitbucket
- AWS (Amazon Web Services)
- Google Cloud Platform
- Microsoft Azure
Cryptocurrency
If you’re involved in cryptocurrency, many exchanges and wallet services support YubiKey:
- Coinbase
- Gemini
- Kraken
- Binance
Identity and Access Management
For enterprise users, many Identity and Access Management (IAM) solutions support YubiKey:
- Okta
- Duo Security
- OneLogin
- Ping Identity
- Microsoft Azure AD
Operating Systems
YubiKeys can also be used for local authentication on various operating systems:
- Windows 10 and 11 (via Windows Hello)
- macOS
- Linux (via PAM modules)
Web Browsers
Modern web browsers support WebAuthn, allowing YubiKey to be used for passwordless login on supporting websites:
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Apple Safari
This list is not exhaustive, and the number of services supporting YubiKey and other FIDO2 compliant security keys is continually growing. It’s always worth checking if a service you use supports hardware security keys, as it’s an excellent way to enhance your overall security posture.
When setting up your YubiKey with these services,
In-Use
The YubiKey 5C Nano offers a mostly seamless and straightforward user experience. Once set up with compatible services, using the key is a simple process:
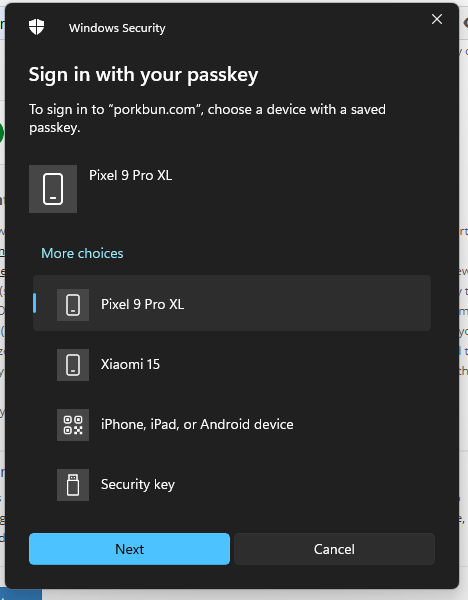
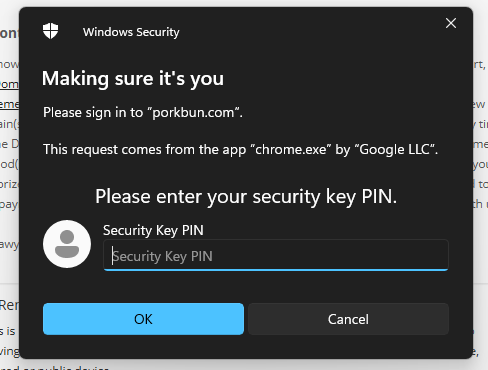
- Insert the YubiKey 5C Nano into a USB-C port on your device.
- When logging into a supported service, enter your username and password as usual.
- Depending on how you have set up MFA and passkeys in the past, you may get a prompt for different options, such as Windows Hello or Bitdefender, or if you select hardware keys, you may have multiple phones to choose from
- In most cases, when you select the hardware key, you will also need to input the security key PIN.
- You then simply tap the small gold button on the top edge of the YubiKey.
- The service will recognise the key’s input and grant access to your account.
While that is a bit more involved than I had hoped, the main issue is that I need to clean up all the different MFA options I have used to streamline the process.
The YubiKey 5C Nano doesn’t require any batteries or network connectivity, ensuring it’s always ready for use. This reliability is particularly valuable in situations where you might not have access to a mobile signal or when your phone’s battery is depleted.
Price and Alternative Options
| Preview | Product | Rating | Price | |
|---|---|---|---|---|

| Yubico - YubiKey 5C Nano - Two-factor authentication (2FA)... |
£65.28 | Buy on Amazon |
The YubiKey 5C Nano is available on Amazon for £64.90 and is also available directly from Yubikey.
The YubiKey 5C NFC is £54.90 and the YubiKey 5 NFC (USB-A) is £49.90.
Yubico also sell the Security Key series, which supports fewer protocols but is much cheaper at £29 for the USB-C model and £25 for USB-A. There is no nano version of this.
There are plenty of competing options, and many of these are more affordable, but they tend to support fewer protocols than the YubiKey 5 series. They are, therefore, more comparable to the Security Key series.
Overall
The Yubikey 5C Nano is a superb hardware security key that excels in portability and versatility. Its support for multiple protocols and services makes it a strong choice for users wanting to be able to use this with as many services as possible.
The authentication process did require more steps than I had hoped, but a lot of that was due to my mess of MFA options.
While the price may be a barrier for some, its durability and ease of use offer long-term value.
The debate over leaving it plugged in is valid but largely mitigated by the need for additional credentials to use the key. For those prioritising convenience and security, the Yubikey 5C Nano is a worthwhile investment.
Yubico Yubikey 5C Nano Review
Summary
The Yubikey 5C Nano is a superb hardware security key that excels in portability and versatility. Its support for multiple protocols and services makes it a strong choice for users wanting to be able to use this with as many services as possible.
The authentication process did require more steps than I had hoped, but a lot of that was due to my mess of MFA options.
While the price may be a barrier for some, its durability and ease of use offer long-term value.
The debate over leaving it plugged in is valid but largely mitigated by the need for additional credentials to use the key. For those prioritising convenience and security, the Yubikey 5C Nano is a worthwhile investment.
Overall
90%-
Overall - 90%90%
Pros
- Comprehensive multi-protocol support
- Broad compatibility with services and platforms
- Simple, battery-free operation
- Compact, discrete form factor
Cons
- Higher price compared to similar options
- Potential security concerns if left plugged in
- Limited to USB-C devices
I am James, a UK-based tech enthusiast and the Editor and Owner of Mighty Gadget, which I’ve proudly run since 2007. Passionate about all things technology, my expertise spans from computers and networking to mobile, wearables, and smart home devices.
As a fitness fanatic who loves running and cycling, I also have a keen interest in fitness-related technology, and I take every opportunity to cover this niche on my blog. My diverse interests allow me to bring a unique perspective to tech blogging, merging lifestyle, fitness, and the latest tech trends.
In my academic pursuits, I earned a BSc in Information Systems Design from UCLAN, before advancing my learning with a Master’s Degree in Computing. This advanced study also included Cisco CCNA accreditation, further demonstrating my commitment to understanding and staying ahead of the technology curve.
I’m proud to share that Vuelio has consistently ranked Mighty Gadget as one of the top technology blogs in the UK. With my dedication to technology and drive to share my insights, I aim to continue providing my readers with engaging and informative content.
Last update on 2025-07-03 / Affiliate links / Images from Amazon Product Advertising API