Any links to online stores should be assumed to be affiliates. The company or PR agency provides all or most review samples. They have no control over my content, and I provide my honest opinion.
How to protect your passwords? Which tool to use? How password managers secure our internet browsing, our mobile devices, and more you can find out here.
Many people do not realize that passwords are needed for something long and strong, especially when we already know that the Internet gives birth to a lot of hackers. But the question is how will we remember our long and ugly passwords?
One might think that the answer is, using the brain, that might be an option, but few people are ready for that. A large number of people have a multitude of passwords on different platforms.
In these cases, the password manager acts like a charm. It can easily and securely store all your passwords, ready to be accessed at any time. Security tools, for example, Keeper Password Manager & Digital Vault may offer your mobile phone or other devices much deeper security. It comes with a variety of features like dark web protection, encrypted chat services, and more, which you can find out reading this article. It offers many features such as Instant login, automatic filling of forms such as payment and shipping information, generates long and strong passwords, and the ability to store insurance cards. This tool uses patented security technology to protect your data and has built-in two-factor authentication for added protection.
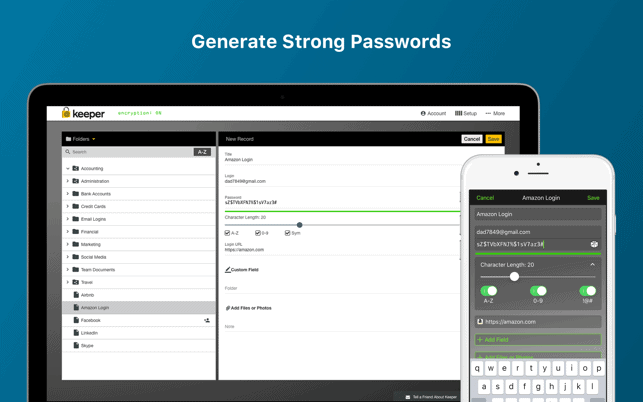
Your passwords are stored in a vault that can be accessed by a master password or key file of the desired setting. Since this tool is open source, everything, including encryption, is transparent. You can check in detail whether all functions are correct or not. I hope the tools will help you troubleshoot your password and be a little more secure in this internet world.
The number of mobile phone users is increasing day by day. Analyzing the history of mobile devices, we can conclude that the manufacturers of mobile devices developed new very sophisticated devices that can rightfully be called smartphones. Due to their increased capacity and number of facts that affect our daily lives, we become more and more dependent on modern mobile phones. Smartphones are used in different ways for a telephone conversation, Internet search, use of various services (SMS, MMS, e-mail), use of cameras, or GPS devices. With the development of mobile technology, there are also the first security problems, which affect the communication channel, ie, data transfer from the sender to the recipient. Security threats to these devices are becoming larger because there is still a lack of adequate security mechanisms and tools for protection. With the use of operating systems for mobile phones, this problem became more complicated. Each operating system brings with it a large number of benefits to users, but also several security vulnerabilities. Having in mind that the Internet via mobile devices is increasingly popular, there are risks related to safe communication and the stage of establishing a communication channel. Due to the increasingly massive use of mobile devices of any participant in communication.
Imagine what would happen if someone got access to all your contacts, photos, social media profiles, messages, and even a bank account? All this is on your mobile phone, and a little carelessness, crowds in public transport, and the dexterity of thieves are enough to experience this nightmare.
If you haven’t set your phone lock by now, summer is the right time to do so. It may not protect your mobile phone from possible theft, but it will at least make it harder for anyone to try to access the data. That’s why it’s best to set your phone lock with a password. The code may involve entering the numbers you have selected, or dragging templates along with the dots that appear on it. More advanced phones can unlock on a fingerprint. Besides, there is an option that if someone repeatedly tries to unlock the phone, the front camera turns on and takes a picture of that person’s face.
You can lock the phone manually after each use, or if you find it easier to automatically protect the phone keypad (keypad lock). Set the time for which the phone will lock automatically. This time is entered by the phone user and can range from a few seconds to a few minutes. It is usually enough for it to be about 10 seconds, or even shorter.
VPN protection is the best form of data protection that is on the mobile phone when traveling. During this period, do not use mobile internet, but usually keep Wifi turned on and look for free networks.
Some hackers make free Wifi precisely because of naive tourists who connect to the network. Of course, this is not about free WiFi networks officially set up by tourist centers. Then all data and passwords from your phone that can be misused can be easily accessed. Fortunately, there is a way to protect yourself from these attacks, and that is the VPN.
Its role is to keep all your data secure even when you log in to unsecured Wifi networks. Hackers will not be able to misuse your data, and depending on VPN protection, you can remain completely unnoticed.
It’s good to have GPS turned on on your phone especially if you’re in an unfamiliar city to get by faster and better. Using maps you can get to a specific destination using the shortest route. Also, GPS will be used in case your phone is stolen. By turning on GPS, you can track your phone, which can help you find it more easily.
We need PIN code protection in case of theft, when in addition to running out of phones, it can happen that, if we are a postpaid user, someone creates an astronomical bill that we have to pay.
Therefore, enable the PIN code request service (personal identification code). If you leave the phone switched off, each time you switch it on, the device asks you to enter the PIN code. If the PIN is entered incorrectly several times in a row, the card will be blocked.
Two out of three people who report cell phone theft do not know the unique number of their device that can be used to identify and track the device. If the police find the thief, the identification number will help you find out if it is your mobile phone.
The IMEI number will be useful to you so that you can block the device if it is stolen. When reporting the theft, the police and the mobile operator must be given this number. Based on your IMEI number, your mobile operator may block your phone so that no one can use it until you find it.
I am James, a UK-based tech enthusiast and the Editor and Owner of Mighty Gadget, which I’ve proudly run since 2007. Passionate about all things technology, my expertise spans from computers and networking to mobile, wearables, and smart home devices.
As a fitness fanatic who loves running and cycling, I also have a keen interest in fitness-related technology, and I take every opportunity to cover this niche on my blog. My diverse interests allow me to bring a unique perspective to tech blogging, merging lifestyle, fitness, and the latest tech trends.
In my academic pursuits, I earned a BSc in Information Systems Design from UCLAN, before advancing my learning with a Master’s Degree in Computing. This advanced study also included Cisco CCNA accreditation, further demonstrating my commitment to understanding and staying ahead of the technology curve.
I’m proud to share that Vuelio has consistently ranked Mighty Gadget as one of the top technology blogs in the UK. With my dedication to technology and drive to share my insights, I aim to continue providing my readers with engaging and informative content.







