Any links to online stores should be assumed to be affiliates. The company or PR agency provides all or most review samples. They have no control over my content, and I provide my honest opinion.
After several data breaches, including the much publicized Cambridge Analytica-Facebook scandal, people are starting to look not just towards social media with increased scrutiny but their own handheld devices, their beloved, multi-functional smartphones, with a mixture of caution and trepidation.
No doubt, we’ll all still continue to use our phones and access apps – who can even remember life before them anymore? But the numbers on online safety, browsing and mobile phone vulnerabilities paint a picture that shows very explicitly just how common data breaches have become – and how unsuspecting we, as users, are about them:
- 67% of organizations have experienced a data breach from employees using their mobile phones to access the company’s data
- In 2016, 1.3 million Google accounts were compromised through illegitimate Android apps
- According to the AV Test Security Report 2016-2017, 643,476 new Android malware programmes had emerged by Jun 2017
- Symantec, the popular software company, reports that there are 24,000 malicious mobile apps blocked every day
- And Accenture reports that, in 2017, there were over 130 large-scale, targeted breaches in the year, which has been growing by 27% every year
- In 2017, 147.9 million consumers were affected by the Equifax Breach
Online safety has been a topic of an evolving nature but now it concerns our smartphones and it’s become about how to mitigate the new reality: One in which attacks are an inevitability and breaches are a certainty.
Use this guide to learn how you can protect yourself in your own created shield of online safety, as long as you recognize the risks and take these steps to mitigate them.
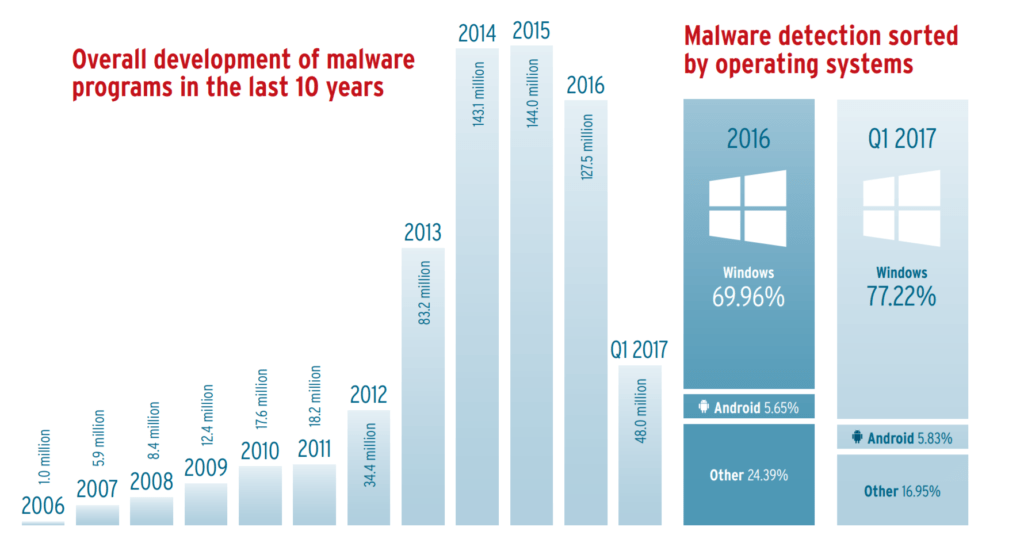
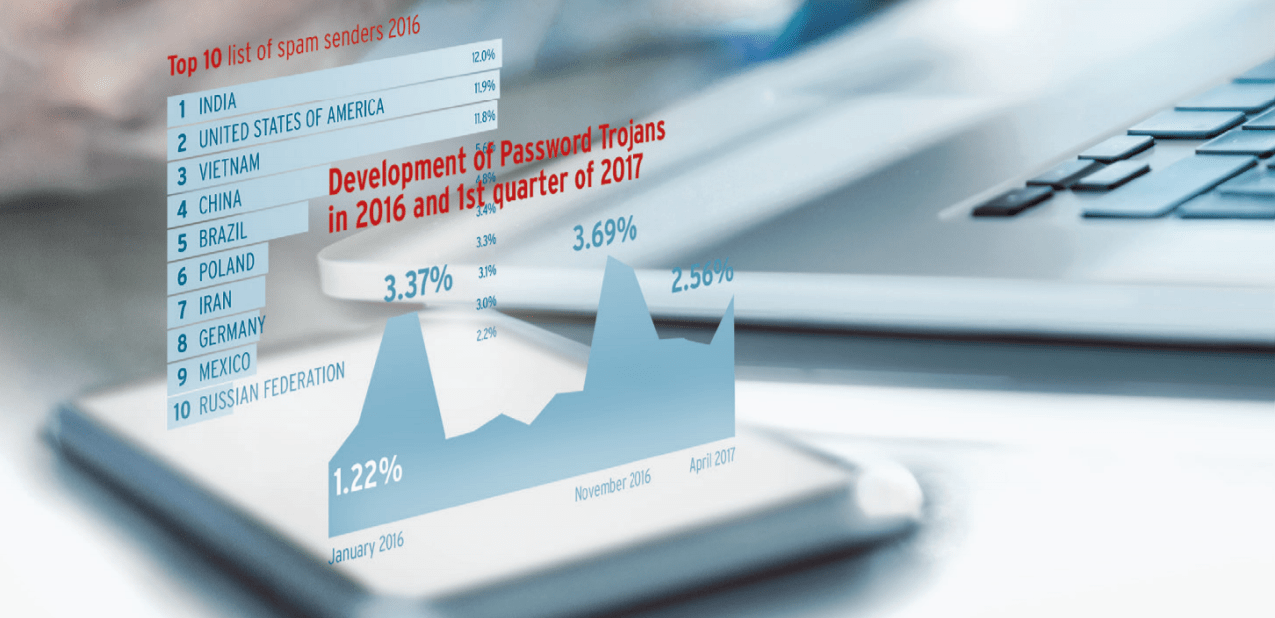
Where do data breaches and security vulnerabilities come from?
The digital realm requires so much more than simply connectivity. The moment we insert humans into the mix, there’s bound to be some chaos, a chance to learn new information and broaden accessibility but an equal chance to capture information in unlawful and invasive ways.
There are a few key dangers, areas which, when we tread without mechanisms of online safety and protection, our private data is at stake. Because 80% of digital natives are smartphone users, scams and data breaches have shifted their attention from the desktop to the mobile world.
Let’s take a look at what these vulnerabilities look like.
Unsecured Wi-Fi
With a rise in the “gig” economy and “location independent” freelancers and their businesses, there are a greater number of users than ever before using their smartphones not just for posting the latest selfie but to actually conduct business over.
These “digital nomads” and freelance business owners often rely no the public networks in cafes, restaurants and outdoor squares to catch up with email, get work done, browse the web and send sometimes sensitive information, files and correspondence across these otherwise open networks.
It’s a matter of convenience but it’s also unadvisable. Public wi-fi exposes your phone, instantly to others who can “game” the network, accessing private or sensitive personal information when you’re on the network. There’s no password encryption and the network is inherently unprotected.
Malware from applications
For the most part, apps that come from your smartphone device’s “app” store are “safe” (up to a certain degree). They’ve at least been vetted and don’t contain other spam or are unlikely to contain other secretive downloads.
However, if smartphone users download apps from places other than their phone’s app store, they could be prone to malware application downloads that can then make them vulnerable to hackers using the application to worm their way into the device’s data.
Phishing sites
These are sites that rely on a user taking an action and then, unwittingly, getting themselves into a situation where they willingly reveal their own personal information. Phishing sites are closely connected to phishing emails, which present an impossible and usually ludicrous situation (some form of a person in trouble who needs some money) and then asks the victim to either help them financially for a greater payout later.
Phishing sites could also present “lures” to users by positioning their website as a free offer, a campaign or a lottery that the user has won. These same sites also use your email to set up fake notices from retailers like Apple, PayPal, banks, and even your country’s tax agency, in order to be able to get you to click their button, give out your information to “log in”and then render yourself vulnerable by your own hand.

Download scams
Desktop users will know all about download scams. For mobile phones, these are usually in the form of apps or downloads for a free resource, in the form of pop-ups. Be aware: downloads can happen, even on your phone so you should exit not just the popup but the site itself.
How to protect yourself while browsing on a smartphone
Now that you know the various ways in which you could be targeted, you’ll be happy to know that there are multiple layers of defense and various tactics you can use, in order to protect yourself while browsing on a smartphone.
1) Activate a screen lock
This is for physical intruders trying to get at your phone, in case you leave it somewhere, or happen to lose it. But, besides just the screen lock that is password protected (or, as on the iPhone X, unlocked through facial recognition), you should also be allowing the device to automatically wipe your data after 10 failed login attempts.
Many phones now have biometrics for unlocking a phone and this is really the feature that makes the most sense. If a hacker does manage to gain access, they can install key logger software, which will simply capture all your typed passwords, including your phone lock password. So opt for a fingerprint or facial recognition as a phone unlock, where possible.
2) Apps and permission
When the Facebook and Cambridge Analytica scandal came up to light, Facebook representatives responded that one of the main ways that data had been leaked was through the unmonitored use of third party apps.
The same goes for your phone. Now that everyone owns a phone and there are lower barriers to entry than ever before for app creation, it’s possible for anyone out there to create apps.
But each app comes with its own “permissions”. Instagram, for example, asks for “permission” to access your microphone and camera. Some apps want access over your location or can be synced with other apps to enable “one-click purchase” or app-to-app integration.
You want to make sure you’re disabling the option to allow the installation of third party apps. You also want to go into your “Settings > Apps” for your smartphone and manually check the kinds of permissions you’ve granted to each app. Reconsider each of these and whether you even granted permission for the use of other features of your device or your personal information in the first place.
3) Install an ad blocker
Your next course of action is to install an ad blocker for your phone. Yes, ads are intrusive and irritating to those who are trying to browse the web but there’s something more sinister going on that you’ll have to address. Ads can be exploited by cybercriminals. It’s known as “malvertising” and it’s a form of delivering ads through servers right on your phone — without you even needing to click anything.
If you’re on an Android, you’re at risk but you also have more control than there smartphone users. In 2018, over 14 million Android devices were infected with CopyCat, malware that was routed through pop-ups, which an ad-block app could have mitigated.
Once you install a useful ad blocker, you’ll want to go to Settings > Site Settings > Pop-ups and make sure the option is set to “Blocked”.
And because so many of these pop-ups are designed through Javascript code, in order to break them down entirely, you can opt to disable Javascript running in your mobile browser.
4) Set up automatic backups
Sometimes, the worst will happen and, despite your best efforts, you’ll encounter a rooted virus that entirely takes over your phone. In this case, all hope is not lost. But to counterpunch that virus, you’ll need to destroy the phone itself — in other words, be prepared to do a factor reset.
Factory resets wipe out data from the phone’s storage and resets the device to its “out of box” settings. It has zero memory of what has happened before.
This wipes out viruses but also has the same effect on your data. So make sure that you’re backing up your phone’s apps, photos and other sensitive data through automatic backups.
You can usually do this to a secure cloud account that comes with the phone (such as iCloud) or set up a backup to link to services like Dropbox or Google Drive.
5) Use two-factor authentication
What is “two-factor authentication”? It’s a process where you concede to having a text message sent to you each time you sign in on a new device, from a new location. This means that, for example, if you were to be traveling and you accessed your Gmail email, two-factor authentication would require you to authenticate that the person signing in is indeed you and not a fraud.
You also want to make sure that you use a randomized pattern for password protection and that each of these codes are used only once.
6) Encrypt your data
Encryption sounds like a big fancy word that only top-secret agents use but, in fact, it’s quite a simple concept.
According to Google, “Full disk encryption is the process of encoding all user data…Once a device is encrypted, all user-created data is automatically encrypted before committing it to disk and all reads automatically decrypt data before returning it to the calling process”
Essentially, once you enable encryption on your phone, your device will then ask you for a password that activates the decryption process. There’s a caveat, however: Forget the password or misremember and only a factor reset will get you back into the system.
7) Rely on a secure connection when you’re checking sensitive information
If you don’t have a data plan or you’re simply traveling and don’t want to turn on data roaming, the best way to secure your connection and the ensure the integrity of your personal information is kept intact is to use private hotspot. Usually, this would mean either using your phone’s data plan or to use a device like Skyroam, in order to access unlimited data at 3G or 4G connection speed.
Of course, Skyroam, though it’s ready and available for travelers in 120 different countries, comes with a cost: The device itself costs around $110 and you’ll have to agree to a “pay as you go plan”.
However, the alternative is to expose your private information and data transfer to the dangers of a public connection — and we already know that that might entail.
When it comes to protecting your browsing experience on a smartphone or preserving the privacy of the data stored on your phone, you can see that there are several tactics that can cover up those points of entry for hackers. However, online safety requires a little planning and forethought. Use a combination of these layers of protection and choose a smartphone that allows you to perform these protective functions and you’ll be able to keep your online safety intact.
We really hope that you improved your cybersecurity knowledge by reading this. Stay up-to-date on online security by reading VPNpro’s blog.
I am James, a UK-based tech enthusiast and the Editor and Owner of Mighty Gadget, which I’ve proudly run since 2007. Passionate about all things technology, my expertise spans from computers and networking to mobile, wearables, and smart home devices.
As a fitness fanatic who loves running and cycling, I also have a keen interest in fitness-related technology, and I take every opportunity to cover this niche on my blog. My diverse interests allow me to bring a unique perspective to tech blogging, merging lifestyle, fitness, and the latest tech trends.
In my academic pursuits, I earned a BSc in Information Systems Design from UCLAN, before advancing my learning with a Master’s Degree in Computing. This advanced study also included Cisco CCNA accreditation, further demonstrating my commitment to understanding and staying ahead of the technology curve.
I’m proud to share that Vuelio has consistently ranked Mighty Gadget as one of the top technology blogs in the UK. With my dedication to technology and drive to share my insights, I aim to continue providing my readers with engaging and informative content.