Any links to online stores should be assumed to be affiliates. The company or PR agency provides all or most review samples. They have no control over my content, and I provide my honest opinion.
I have covered quite a lot of cyber security related news and reviews of the past few years, and the issues with cybersecurity appear to be growing exponentially.
Cybercrime is extremely lucrative and arguably a lot safer than traditional criminal activities. Ten years ago, it may have been some teenager sat in his bedroom hacking your computer, but nowadays it is likely an organised criminal network.
As consumers put their lives online via social media, and households become increasingly connected with IoT devices there are more opportunities than ever for cybercriminals to exploit.
In the consumer world getting hacked is a terrible thing, but most of the time it is more of an inconvenience or a small cost. In the enterprise world, however, any form of cybersecurity breach can cost millions, or even ruin a business and can affect hundreds of people if not thousands.
It feels like there is almost a weekly occurrence of a major cybersecurity incident if you read the news. On BBC News in the last six weeks, there have been at least three data breach stories including Cathay Pacific having 9.4 million user details accessed, Uber paying $148m over a data breach cover-up, and Equifax fined by ICO over a data breach.
Then there was the WannaCry ransomware attack which affected more than 200,000 computers across 150 countries, with total damages ranging from hundreds of millions to billions of dollars.
Account Takeover (ATO) Attacks
![]()
One of the popular exploits that cybercriminals are increasingly using is Account Takeover (ATO) attacks. These are quite a simple method of attack where a criminal will gain access to the login details either via phishing, basic exploits or through buying the data on the black market.
Many people use the same login details across platforms, so if a member of staff uses their business email to log in to LinkedIn as well as corporate systems, and the criminal gets access to the LinkedIn details they can then easily access the corporate network.
Account Takeover (ATO) affects both consumers and companies alike, but if an individual within a company suffers from an ATO then the consequences can be catastrophic. Once the account has been taken over the criminal can use the account to send out more phishing emails all coming from a valid corporate address. This then allows the breach to expand to more employees within the company. Once the corporation has had its login data exposed it can be possible to gain access to extremely sensitive data which is then often sold on the darknet.
22% of ATO incidents happened to employees in sensitive departments, such as HR, IT, finance, and legal showing that criminal have a strong preference for more sensitive areas, as those sectors have more important personal and financial information.
SpyCloud ATO Prevention
Services such as SpyCloud aim to significantly reduce the risk of account takeovers within a corporate environment. They offer multiple services to identify ATO risks and mitigate the damage caused by them. While the service does not necessarily stop a breach of the user account details, it should avoid an account take over by identifying and blocking compromised accounts.
The SpyCloud system can work in many ways, this includes an Active Directory (AD) tool to run continuously based on your schedule. The tool automatically compares newly stolen credentials to your active employees and forces a password reset when the passwords have been compromised.
You can use the SpyCloud API to integrate the services within apps which will check credentials every time a user logs in, this will then either allow the user in if the account is not exposed or force a password reset or 2FA code if it is believed to be exposed.
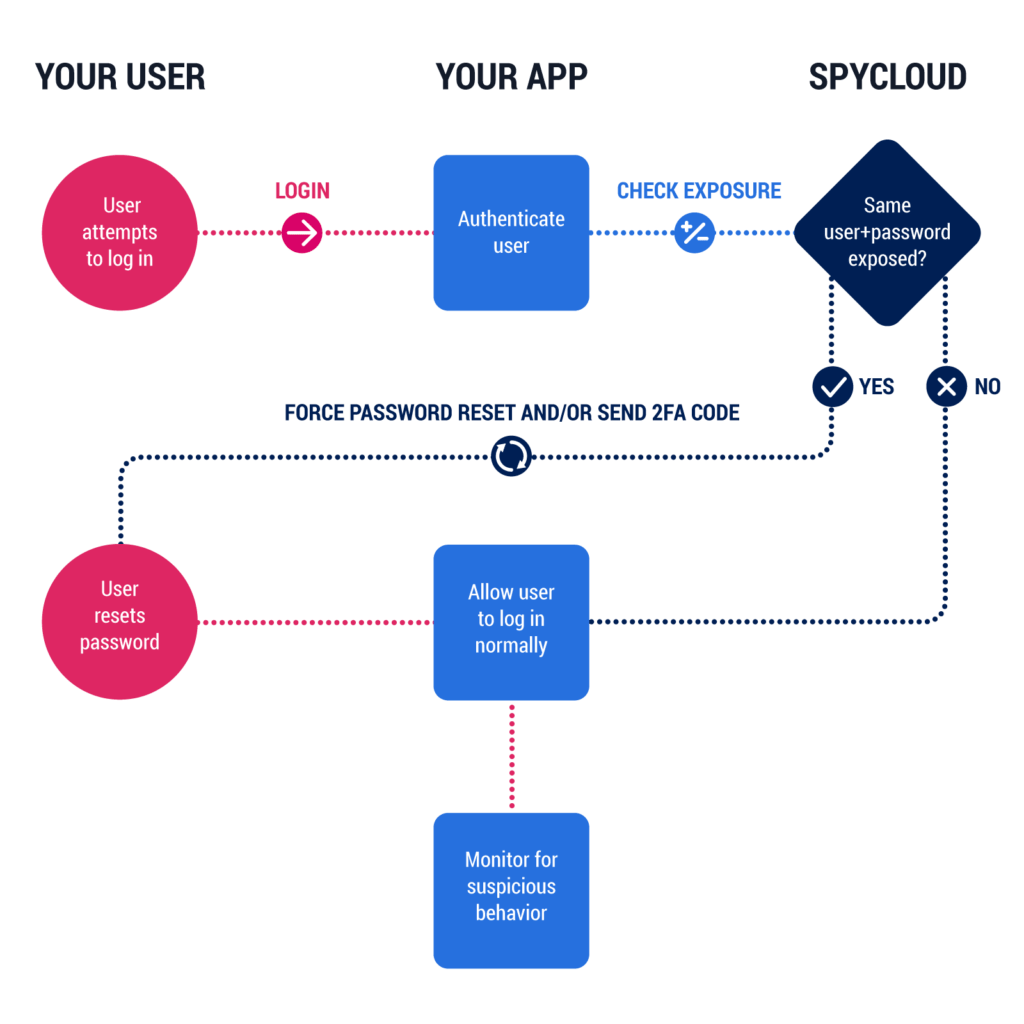
So, for example, if you a company were to have a publicly accessible login system and this then got hit with an ATO tool such as Sniper. If the user’s account has been comprised the login will be run through he SpyCloud system and it will get flagged forcing the user to do a password reset via an email link.
Every time a data breach is published online either publicly or via the darknet, Spycloud will download the data and cross-reference this against the corporate data allowing companies to identify potential breaches.
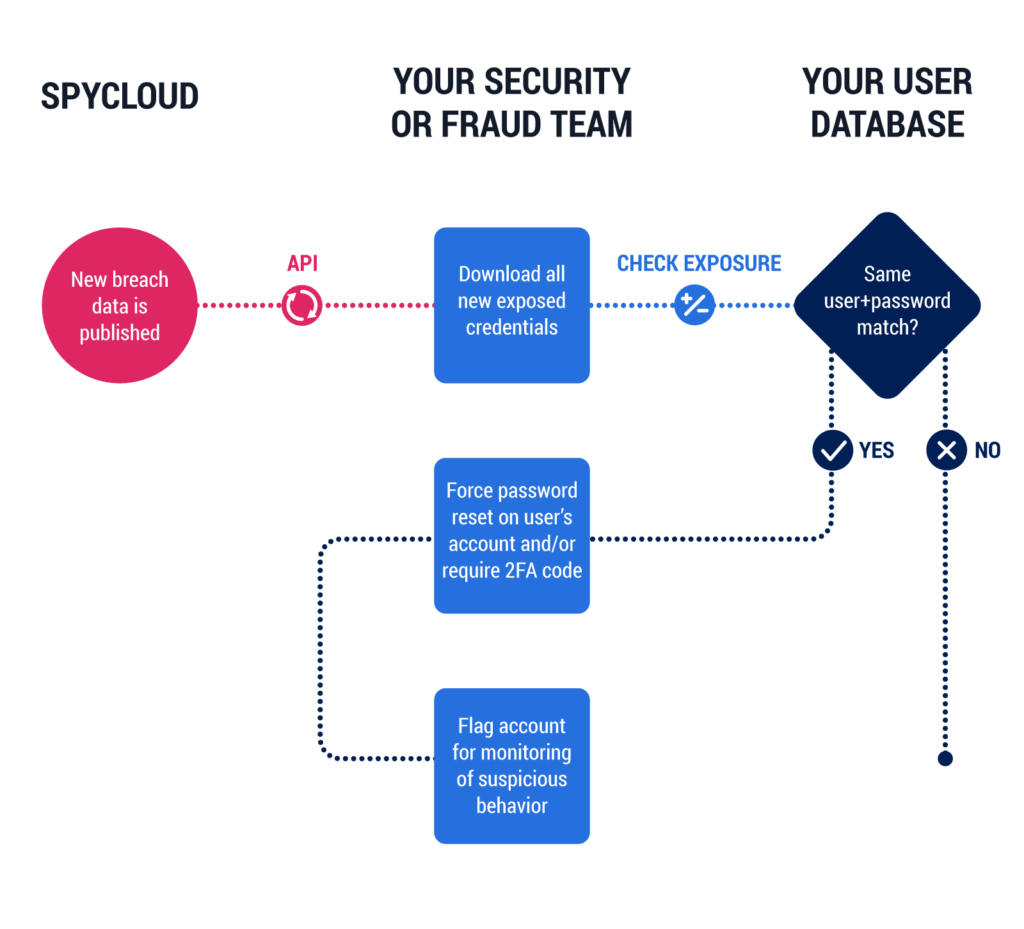
The Spycloud database is one of the largest repositories of decrypted compromised credentials in the world consisting of over 10.5 billion emails and growing, this allows them to identify compromised accounts with a higher success rate than many other companies.
With SpyCloud actively protecting the system it can also be used to enforce secure passwords when a user creates or updates a password this includes checking the password against the compromised account list, avoiding dictionary words, and fewer than 8 characters.
Implementing SpyCloud into an existing system is extremely simple, the company offers multiple code examples and extensive documentation to help you implement it in systems on various platforms including PHP, Python, Java and many more.
SpyCloud is so effective at what it does they are used by some of the biggest tech companies in the world including Cisco and Automattic (the company behind WordPress).
If the service is of interest to you, SpyCloud offer a free customised demonstration and trial of their service so you can test it and see how easy it is to integrate into your current system.
Go to SpyCloud.com to learn more about SpyCloud ATO Prevention or request a free trial
I am James, a UK-based tech enthusiast and the Editor and Owner of Mighty Gadget, which I’ve proudly run since 2007. Passionate about all things technology, my expertise spans from computers and networking to mobile, wearables, and smart home devices.
As a fitness fanatic who loves running and cycling, I also have a keen interest in fitness-related technology, and I take every opportunity to cover this niche on my blog. My diverse interests allow me to bring a unique perspective to tech blogging, merging lifestyle, fitness, and the latest tech trends.
In my academic pursuits, I earned a BSc in Information Systems Design from UCLAN, before advancing my learning with a Master’s Degree in Computing. This advanced study also included Cisco CCNA accreditation, further demonstrating my commitment to understanding and staying ahead of the technology curve.
I’m proud to share that Vuelio has consistently ranked Mighty Gadget as one of the top technology blogs in the UK. With my dedication to technology and drive to share my insights, I aim to continue providing my readers with engaging and informative content.