Any links to online stores should be assumed to be affiliates. The company or PR agency provides all or most review samples. They have no control over my content, and I provide my honest opinion.
Garmin is still recovering from its recent ransomware attack which took down their IT systems for several days. At the time, it had me questioning how such a large organisation could suffer such a significant ransomware attack?
Days after this incident, another multinational company has fallen victim to such an attack. BleepingComputer has once again brought news of the attack to the public which has resulted in the loss of data for users of their free 10GB storage feature.
It looks like only some of Canon’s systems have fallen foul to this ransomware, but still a lot of them. This includes Canon’s email, Microsoft Teams, USA website, and other internal applications.
It looks like Canon have been just as bad as Garmin with informing their customers about the attack.
Image.canon loses terabytes of data
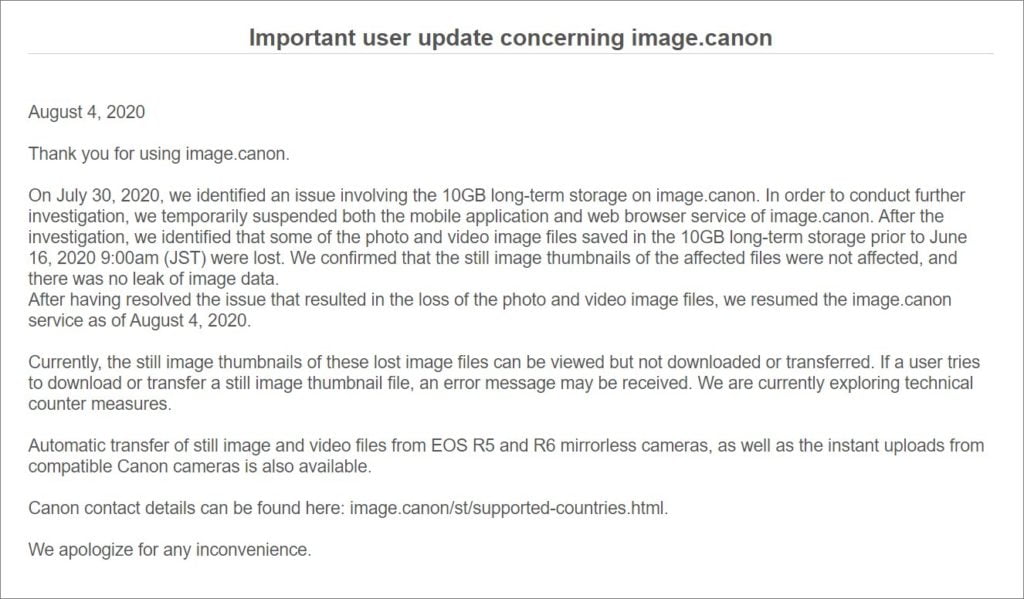
The image.canon site suffered an outage on July 30th, 2020, and over six days, the site would show status updates until it went back in service on August 4th.
Canon then published a vague statement on the 4th, stating that an issue occurred and that they suspended access to the image.canon site. They make no mention of a cyber attack but just state that some of the images have been lost, with only thumbnails remaining.
A source for BleepingComputer shared an image confirming wide spread system issues affecting multiple applications, Teams, Email, and other systems may not be available at this time.
Maze ransomware
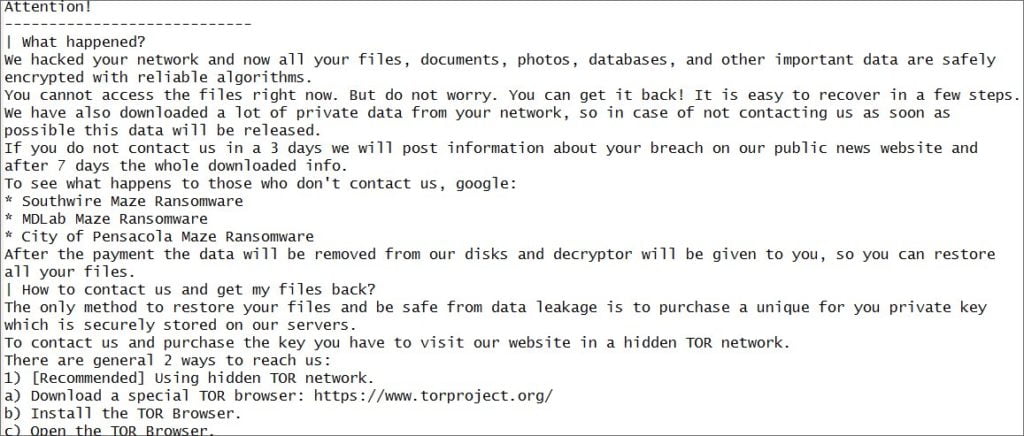
BleepingComputer has also acquired a screenshot of the ransomware note which identifies itself as the Maze ransomware. This is different to the WastedLocker attack that caught Garmin out.
BleepingComputer was told by Maze that their attack was conducted this morning when they stole “10 terabytes of data, private databases etc” as part of the attack on Canon.

Maze uploads user data before encrypting victims drives
Maze will upload any unencrypted data it deems valuable to servers owned by the attackers prior to encrypting the victims drive. So if the ransomware is not paid, Maze will have effectively destroyed the data within the company and release the data on a site they control. A GDPR nightmare.
Maze claim their attack is nothing to do with the issues on the image.canon site.
Maze has claimed responsibility for other high-profile victims in the past, including LG, Xerox, Conduent, MaxLinear, Cognizant, Chubb, VT San Antonio Aerospace, the City of Pensacola, Florida, and more.
Canon has also issued an internal statement confirming the ransomware, but, similar to Garmin, this has not been a public announcement.
GDPR rules from the ICO
Currently, if a personal data breach has occurred, you need to establish the likelihood and severity of the resulting risk to people’s rights and freedoms. This needs to be done within 72 hours of the breach being identified. If you take longer than this, you must give reasons for the delay.
Verbatim from the ico.org.uk website:
If a breach is likely to result in a high risk to the rights and freedoms of individuals, the GDPR says you must inform those concerned directly and without undue delay. In other words, this should take place as soon as possible.
When informing an individual, the company must:
- a description of the likely consequences of the personal data breach; and
- a description of the measures taken, or proposed to be taken, to deal with the personal data breach and including, where appropriate, of the measures taken to mitigate any possible adverse effects.
Failing to notify a breach when required to do so can result in a heavy fine up to 10 million euros or 2 per cent of your global turnover.
I am James, a UK-based tech enthusiast and the Editor and Owner of Mighty Gadget, which I’ve proudly run since 2007. Passionate about all things technology, my expertise spans from computers and networking to mobile, wearables, and smart home devices.
As a fitness fanatic who loves running and cycling, I also have a keen interest in fitness-related technology, and I take every opportunity to cover this niche on my blog. My diverse interests allow me to bring a unique perspective to tech blogging, merging lifestyle, fitness, and the latest tech trends.
In my academic pursuits, I earned a BSc in Information Systems Design from UCLAN, before advancing my learning with a Master’s Degree in Computing. This advanced study also included Cisco CCNA accreditation, further demonstrating my commitment to understanding and staying ahead of the technology curve.
I’m proud to share that Vuelio has consistently ranked Mighty Gadget as one of the top technology blogs in the UK. With my dedication to technology and drive to share my insights, I aim to continue providing my readers with engaging and informative content.